【免责声明】
- 本教程仅供学术研究及逆向工程技术探讨,使用者须确保自身行为符合所在司法管辖区法律法规
- 任何个人/机构不得将所述技术用于破解正版软件、侵害著作权等非法用途,由此产生的法律责任由实施者完全承担
- 禁止将本教程内容用于商业目的或非法牟利,禁止制作/传播破解衍生作品
- 实验性文件下载后须在24小时内彻底删除,不得留存副本或进行二次分发
- 作者不担保技术安全性,不对任何滥用行为及后果承担民事/刑事责任
- 如有侵权请联系<alanhays0617@gmail.com>删除。
下载
MD5: 8900217D5CC8CA008D694735009A3B92
SHA-1: 50F67CAD40B64A9B8854EC6179F244DF6A8139FB
SHA-256: F59FEB121509639C16A8A86AFA9F339E8AE5572DCDDB69500A6C2E68AD4EA7BB
JEB Decompiler PRO 3.19.1 (May 7, 2020) by PNF Software
下载地址:https://www.mirrored.to/multilinks/dojzbtvua6
激活
启动对应的脚本,windows 系统是 jeb_wincon.bat其他系统应该都知道是那个文件。
接着提示输入 jeb password 则输入 ilbtcdnwiuypbzeo,然后点击 Manual Key Generation接着复制 License Data;
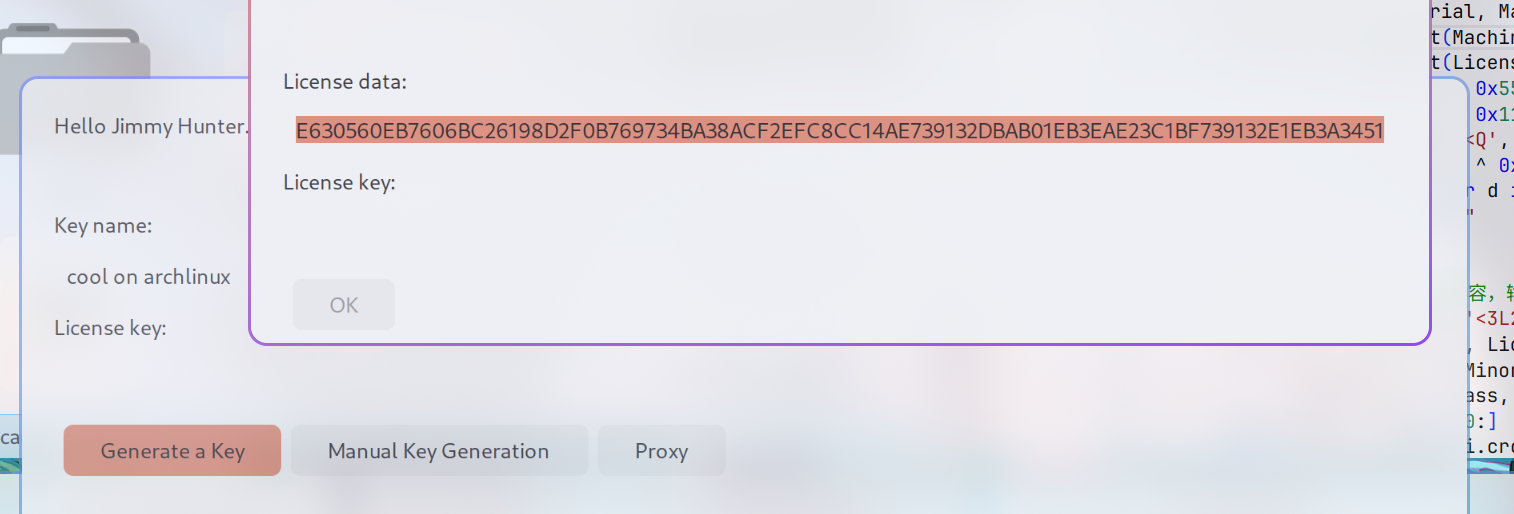
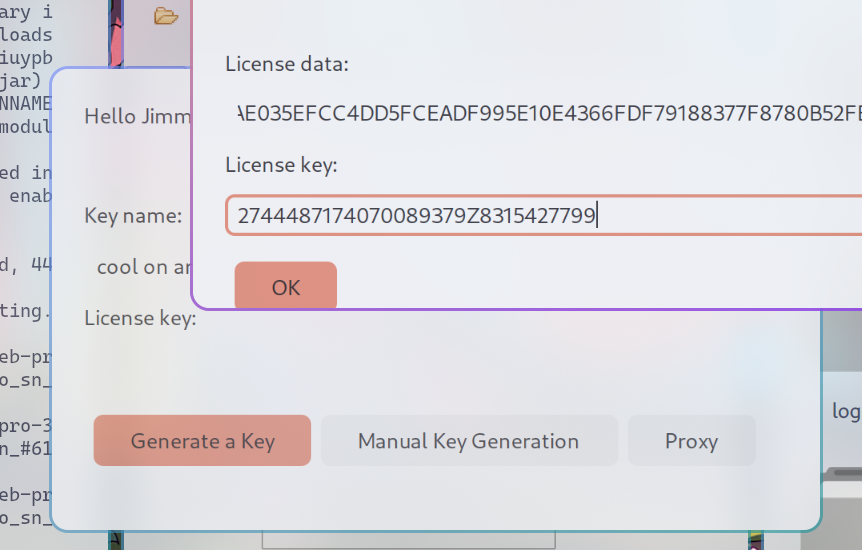
使用 python3 执行下方代码 按要求填入 License Data计算得到 License Key

1 | #https://bbs.pediy.com/ |
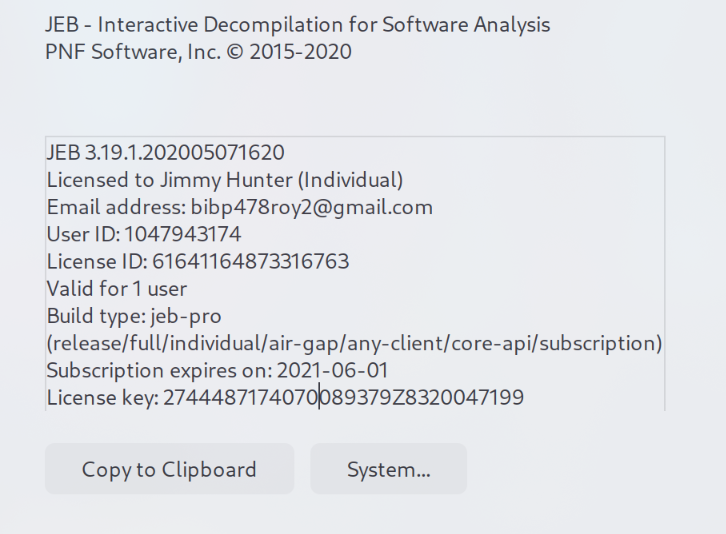
将License Key填入激活
其他版本
mod by CXV
JEB Decompiler 4.29.0.202304042205
https://pixeldrain.com/u/x7EYnhEV
JEB Decompiler 4.32.0.202306131555
https://pixeldrain.com/u/uttjeNgK
JEB Decompiler 5.0.0.202308071454
https://pixeldrain.com/u/pmyKsFyx
https://pixeldrain.com/u/6c9PcT7Y (Android debugger fix and native emulator) and duplicate code tabs fix NEW!
JEB Decompiler 5.14.0.202406122044
https://pixeldrain.com/u/pp6suXFe
https://pixeldrain.com/u/VJ9X1TzJ (FIX unpack to jeb folder and owerwrite)
JEB Decompiler 5.16.0.202408261745
https://pixeldrain.com/u/AsLuzdRE
JEB Decompiler 5.22.0.202412102010